GitOps-Driven Management of VKS Clusters: Enabling GitOps on VCF 9.0 (Part 03)
In the Part-02 blog, we walked through the process of deploying an Argo CD instance within a vSphere Namespace on VMware Cloud Foundation (VCF) 9.0, enabling a GitOps-based approach to manage Kubernetes workloads in a vSphere environment. With Argo CD successfully installed, we now have a powerful toolset to drive declarative infrastructure and application delivery.
In this blog post, we’ll take the next step by demonstrating how to provision and manage VKS clusters directly through the Argo CD UI and CLI. This allows us to fully operationalise GitOps within the private cloud, delivering consistency, scalability, and automation across the Kubernetes lifecycle.
Importance of Managing the Kubernetes Cluster with a Gitops Approach
Adopting a GitOps-based approach for managing Kubernetes clusters enables declarative, version-controlled, and automated operations by leveraging Git as the source of truth for the desired cluster state.
All Kubernetes manifests — including deployments, services, and configuration — are stored and versioned in a Git repository, allowing infrastructure changes to follow the same review, approval, and rollback processes as application code. By decoupling deployments from imperative cluster creation and manual interventions, GitOps delivers a scalable, consistent, and repeatable operational model for Kubernetes across development, staging, and production environments.
Foundational Guide to Deploying and Operating VKS via Argo CD
- Supervisor Cluster:- Ensure the vSphere Supervisor Cluster is enabled and in a healthy state.
- Argo CD Operator + Argo CD instance:- Argo CD Operator and instance must be active and in a healthy state within the Supervisor Cluster.
- CLI:- Ensure the Argo CD CLI and the kubectl / VCF are installed on the bootstrap node.
- Git Repository Access:- Make sure a Git repository is available to store the configuration YAML files and is accessible from the Supervisor Cluster. This repository will serve as the source of truth for all your GitOps-driven deployments.
Here we will cover two key scenarios to showcase the full potential of Argo CD in managing VMware Kubernetes Clusters (VKS)
- Provisioning a new VKS cluster using the Argo CD CLI.
- Creating a new VKS cluster through the Argo CD UI for a more visual and user-friendly approach.
Attaching vSphere Namespace on Supervisor to ArgoCD
As the Supervisor Cluster serves as the management plane for overseeing the lifecycle of workload clusters, we will now attach all relevant vSphere namespaces that need to be managed by the Argo CD instance.
****** Login to the Supervisor Cluster *********
# kubectl vsphere login --server xx.xx.xx.xx --vsphere-username administrator@vsphere.local --insecure-skip-tls-verify
Password:
Logged in successfully.
You have access to the following contexts:
carbon
svc-argocd-service-domain-c10
*** Login to the Argo CD CLI ******
# argocd login 192.168.30.10 --insecure
Username: admin
Password:
'admin: login' logged in successfully
****** Attach the vSphere Namespace on the Supervisor to the ArgoCD Instance ****
# argocd cluster add <supervisor-vip-ip> --namespace <namespace>
WARNING: This will create a service account `argocd-manager` on the cluster referenced by context `xx.xx.xx.xx` with full namespace-level privileges. Do you want to continue [y/N]? y
supervisor cluster
--system-namespace is not supported when it is Supervisor Cluster, we will create serviceaccount argocd-manager in ArgoCD namespace kubernetes resource management
Start permission checking for managing namespace of Supervisor Cluster
INFO[0009] ServiceAccount "argocd-manager" created in namespace "xxxxx"
INFO[0009] RoleBinding "xxxx/xxxx-argocd-manager-role-binding" created
INFO[0009] Created bearer token secret for ServiceAccount "argocd-manager"
Namespace <xxxxxxx>from Cluster 'https://xx.xx.xx.xx:443' addedProvisioning VKS Clusters via Argo CD CLI
To streamline and automate cluster lifecycle operations, we can create VKS (VMware Kubernetes Service) clusters directly using the Argo CD CLI. This approach enables declarative management of cluster resources, making it easier to integrate cluster creation into GitOps workflows. By leveraging Argo CD’s CLI capabilities, we can define and deploy cluster configurations stored in Git repositories, ensuring consistent and repeatable cluster provisioning.
To create a workload cluster YAML file, refer to the Workload Cluster Creation YAML guide. This resource provides detailed information on the required parameters and associated options, which can be used to define and customise your workload cluster configuration effectively.
In this example, I’ve created a sample workload cluster YAML file and uploaded it to GitHub. This file will be used to demonstrate the creation of clusters using both the Argo CD CLI and UI.
*** Argo CD command line to create the application using CLI *******
# argocd app create vks-cli --repo https://github.com/xxxxxx/vks-argocd-cluster.git --path create-tkg-cluster-yaml-files --dest-server https://<supervisor-ip>:443 --dest-namespace carbon --sync-policy automated
application 'vks-cli' created
**** Verifying the application status ********
# argocd app list
NAME CLUSTER NAMESPACE PROJECT STATUS HEALTH SYNCPOLICY CONDITIONS REPO PATH TARGET
carbon/vks-cli https://xx.xx.xx.xx:443 carbon default Synced Healthy Auto <none> https://github.com/xxxxxx/vks-argocd-cluster.git create-tkg-cluster-yaml-files
The Application will start to create on the UI.
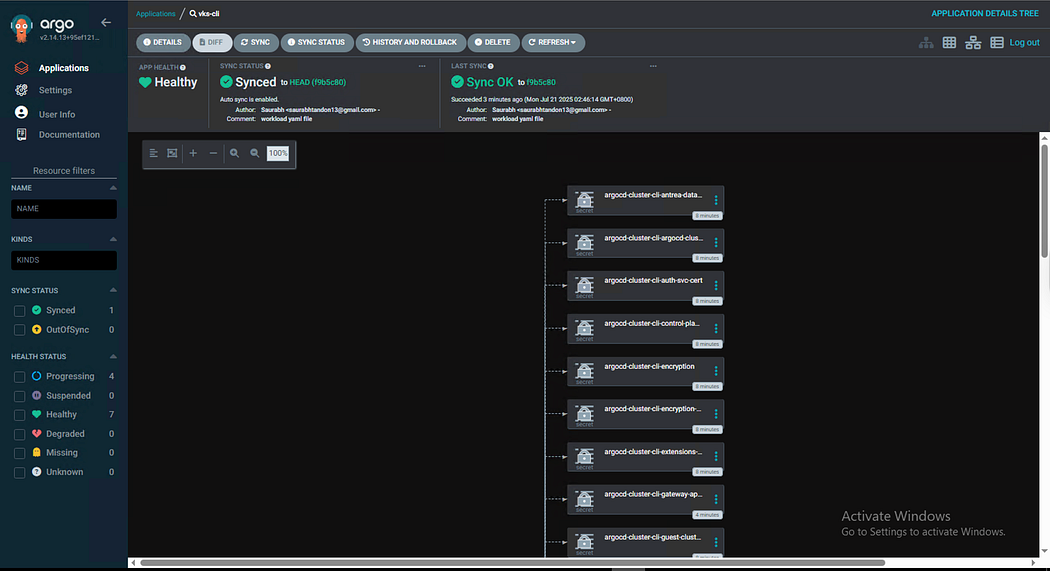
VKS clusters provisioned successfully.
Provisioning VKS Clusters via Argo CD UI
Argo CD’s intuitive web-based UI makes it simple to provision VKS (VMware Kubernetes Service) clusters with minimal manual effort. By linking your Git repository that contains the workload cluster YAML definitions, you can visually manage and deploy clusters directly from the Argo CD dashboard. The UI allows you to select the appropriate project, set synchronization policies, and monitor the deployment status in real time. This user-friendly interface is ideal for teams who prefer a visual approach to GitOps while still benefiting from automated, declarative cluster management.
- Log in to Argo CD UI
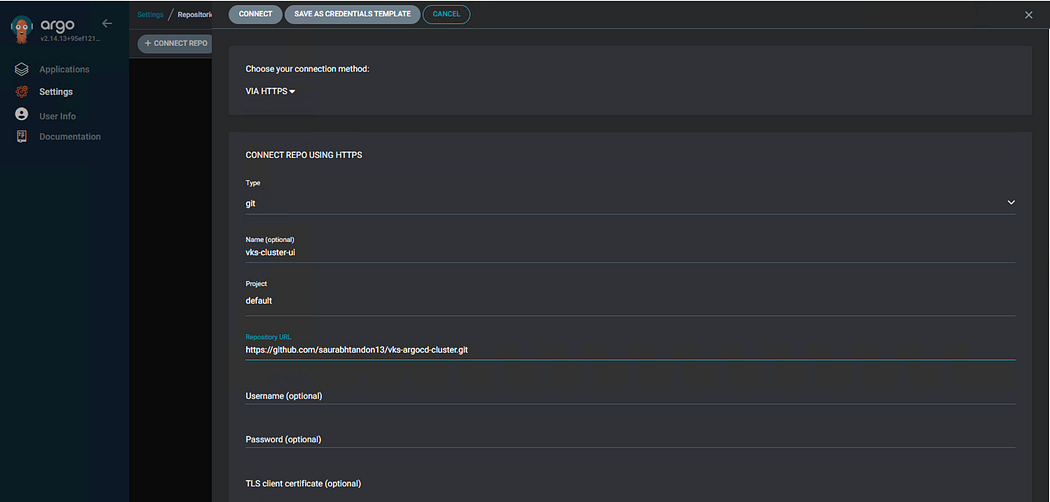
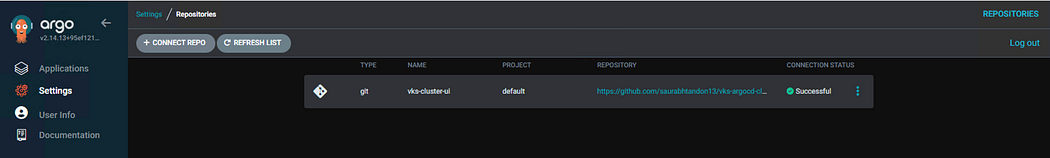
- Click on “Settings” → “ Repositories” → “Connect Repo”. Enter the details and click Connect, and then click “ Create”.
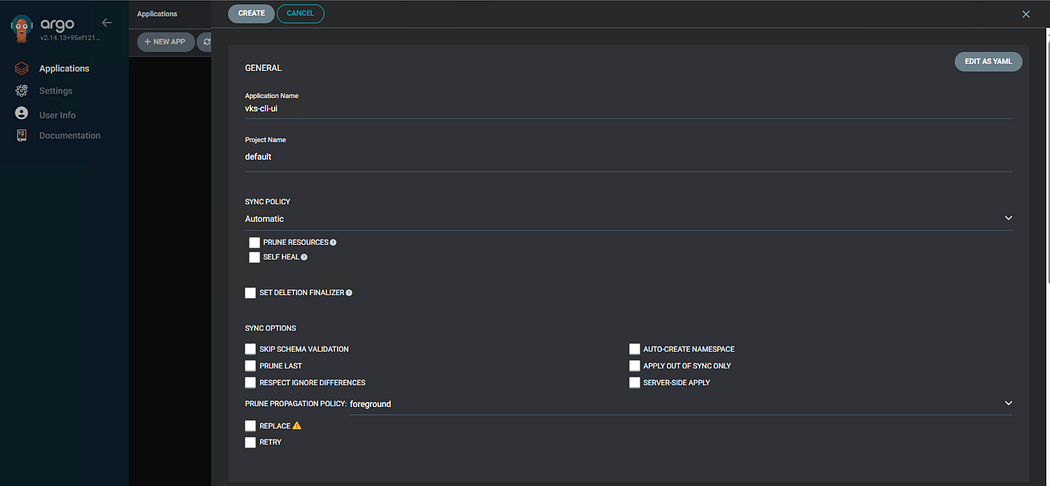
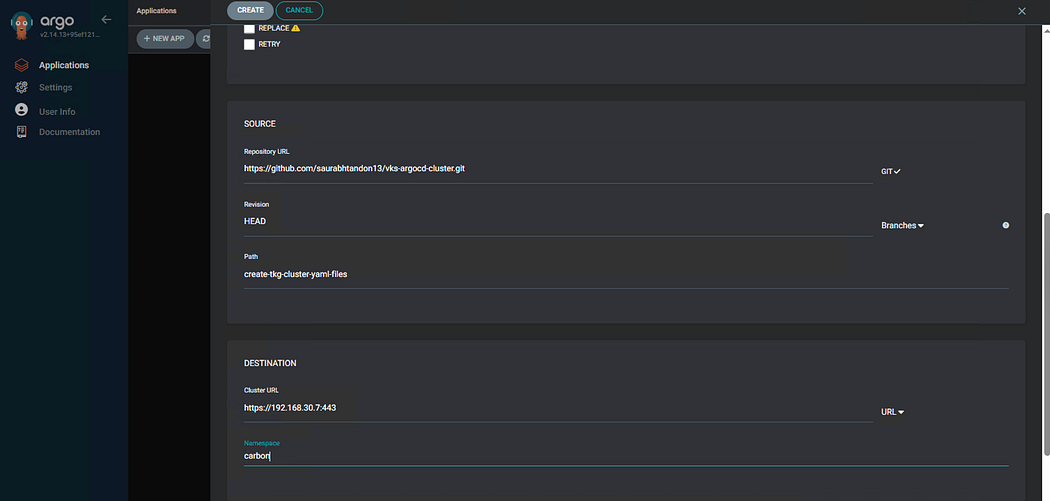
- Click on “Application” → “New App” & Enter the details as shown below
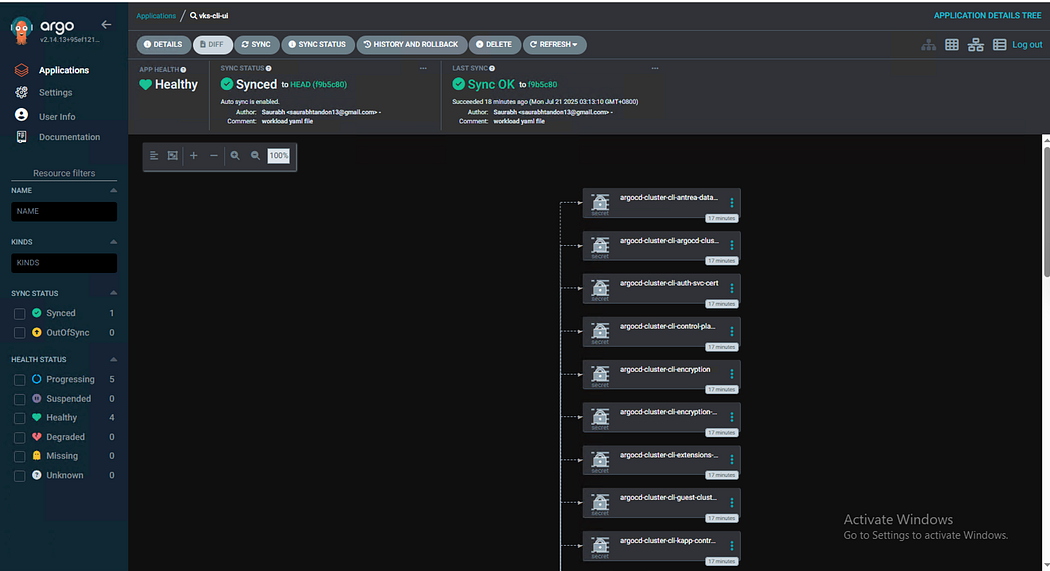
VKS clusters provisioned successfully.

Conclusion
In this blog, we explored how integrating Argo CD with VMware Kubernetes Service (VKS) enables a robust and flexible GitOps workflow for managing both cluster lifecycles and application deployments. Whether you prefer the automation of the CLI or the visual simplicity of the UI, Argo CD ensures consistent, repeatable, and version-controlled operations throughout your vSphere environment.
In the next blog, we’ll dive into more advanced topics, including integrating Argo CD with an OIDC provider for authentication and configuring Argo CD to use a custom certificate for secure access.
Comments
Post a Comment